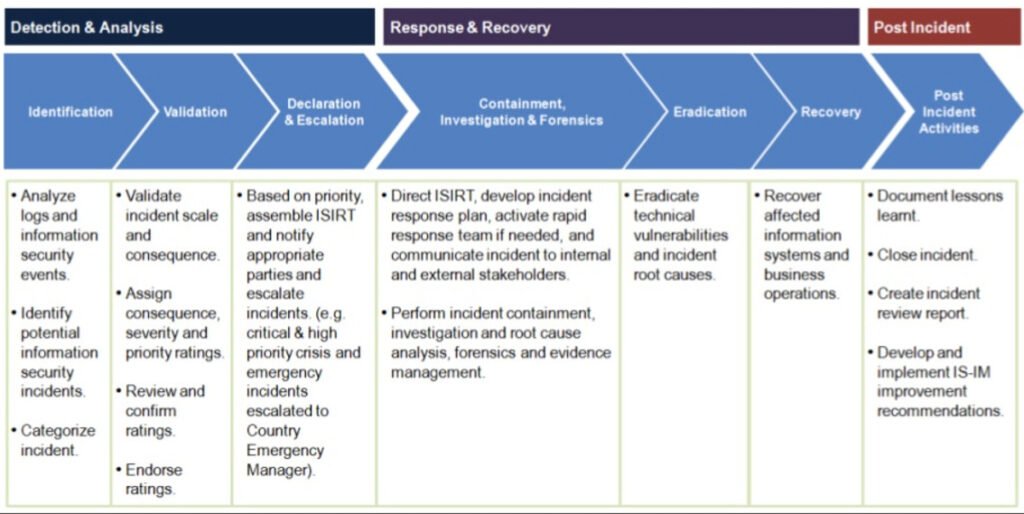
When dealing with cybersecurity, it’s important to know about exfiltration in incident response articles. Exfiltration in incident response article refers to how data is taken from a system during a security incident. This can happen when attackers steal sensitive information, and understanding it can help you protect your data better.
In this blog post, we will break down what exfiltration means in the context of incident response. We’ll look at how it happens, real-life examples, and simple tips to prevent it from affecting your organization. If you’re curious about keeping your data safe, you’re in the right place!
What is Exfiltration in Incident Response?

Exfiltration in incident response is when attackers steal data from a computer system during a security incident. This process involves taking sensitive information from the organization’s network and moving it to an external location. It’s a serious threat because it can lead to data breaches and loss of important information.
Understanding exfiltration is crucial for protecting your data. It helps you know how attackers operate and what methods they use to access and steal information. By learning about these techniques, you can better prepare your defenses and prevent similar attacks in the future.
Companies must be aware of how exfiltration in incident response can occur. Attackers often use various methods like phishing, malware, or exploiting vulnerabilities. Keeping track of these methods can help organizations stay one step ahead and safeguard their data from being stolen.
How Exfiltration in Incident Response Articles Help You Understand Data Theft
Exfiltration in incident response articles provide valuable insights into how data theft happens. These articles explain the different ways attackers can extract data and what organizations can do to prevent it. They serve as a guide for understanding the risks and preparing for potential security breaches.
Reading about real-life examples in these articles can help you recognize warning signs of data theft. They often include stories about companies that faced attacks and how they responded. This knowledge can be used to strengthen your own security measures and avoid making similar mistakes.
Exfiltration in incident response articles are not just theoretical; they offer practical advice on how to handle data breaches. By following the tips and best practices shared in these articles, you can improve your organization’s ability to respond to and recover from attacks.
3. Common Methods of Exfiltration in Incident Response
Exfiltration in incident response article involves various methods that attackers use to steal data. Common techniques include phishing emails, malware, and exploiting software vulnerabilities. These methods allow attackers to access and transfer data without being detected.
Phishing is one of the most common methods used for data theft. Attackers send emails pretending to be from trusted sources, tricking users into revealing sensitive information. This method can be highly effective if users are not cautious and fail to recognize suspicious messages.
Another method is using malware to extract data. Attackers can infect a computer with malicious software that secretly collects and sends data to external servers. Protecting your systems from malware through regular updates and antivirus programs can help prevent this type of exfiltration.
Why Exfiltration in Incident Response Articles Matter
Exfiltration in incident response articles matter because they provide crucial information about how data theft can impact organizations. These articles help businesses understand the risks and consequences of data breaches, making it easier to develop effective security strategies.
Articles on this topic often include expert opinions and case studies that illustrate the real-world impact of data exfiltration. By learning from these examples, organizations can see the importance of having a strong incident response plan in place to handle potential breaches.
Moreover, these articles help raise awareness about the latest trends in data theft. Staying informed about new methods and attack techniques can help businesses stay ahead of cybercriminals and protect their valuable information more effectively.
Real-Life Examples of Exfiltration in incident response article
Real-life examples of exfiltration in incident response provide concrete evidence of how data theft occurs. These cases show the methods used by attackers and the impact on the affected organizations. They help illustrate the seriousness of data breaches and the importance of effective incident response.
One notable example is a company that experienced a major data breach due to phishing. Attackers sent fake emails to employees, leading to the theft of sensitive customer information. This incident highlights the need for strong email security and user education.
Another example involves malware that was used to exfiltrate data from a corporate network. The malware secretly collected and transmitted sensitive data, resulting in a significant security breach. This case underscores the importance of using up-to-date antivirus software and monitoring for unusual activity.
How to Recognize Exfiltration in Incident Response
Recognizing exfiltration in incident response is essential for detecting and responding to data theft. Some signs that data might be exfiltrated include unusual network activity, unexpected file transfers, and access to sensitive information by unauthorized users.
Monitoring network traffic for suspicious behavior can help identify potential data breaches. If you notice any unusual spikes in data transfer or unfamiliar access patterns, it could indicate that exfiltration is occurring.
Additionally, keeping an eye on file access and modification logs can reveal if sensitive information is being accessed or moved without authorization. Regularly reviewing these logs and setting up alerts for unusual activities can help you quickly detect and address exfiltration attempts.
Preventing Exfiltration in incident response article: Easy Steps
Preventing exfiltration in incident response involves implementing several key security measures. Start by ensuring that your organization has a robust cybersecurity framework in place. This includes firewalls, antivirus software, and regular system updates to protect against vulnerabilities.
Employee training is also crucial. Make sure your team is aware of phishing tactics and other common methods used for data theft. Regular security awareness programs can help staff recognize and avoid potential threats.
Setting up strict access controls and monitoring systems can further prevent exfiltration. Limit access to sensitive data to only those who need it and regularly review permissions. Implementing these practices can significantly reduce the risk of data theft and improve your overall security posture.
Tools for Detecting Exfiltration in incident response article
Using the right tools is essential for detecting exfiltration in incident response. There are various security tools available that can help monitor and protect your data from being stolen. These tools can detect unusual activity and alert you to potential threats.
One useful tool is a data loss prevention (DLP) system, which helps monitor and control the transfer of sensitive information. DLP systems can track data movements and prevent unauthorized access or transmission.
Intrusion detection systems (IDS) and intrusion prevention systems (IPS) are also valuable. These systems analyze network traffic for signs of malicious activity and can block potential threats before they cause damage. Using these tools can help you stay alert to any exfiltration attempts.
The Role of Exfiltration in Incident Response Plans
Exfiltration in incident response article plans plays a crucial role in preparing for and managing data breaches. An effective incident response plan should include specific steps for handling exfiltration incidents, ensuring that your team knows how to respond quickly and effectively.
Your incident response plan should outline procedures for detecting exfiltration, containing the breach, and recovering stolen data. It’s also important to include communication strategies for informing stakeholders and regulatory bodies about the incident.
Regularly updating and testing your incident response plan is key to ensuring its effectiveness. Conducting mock drills and reviewing past incidents can help refine your response strategies and improve your ability to handle real exfiltration events.
How Exfiltration in Incident Response Affects Businesses
Exfiltration in incident response article can have serious effects on businesses. Data breaches often result in financial losses due to regulatory fines, legal fees, and damage control efforts. Additionally, businesses may face reputational damage that can lead to loss of customer trust and decreased sales.
The impact on business operations can also be significant. Recovering from a data breach may involve extensive time and resources, affecting productivity and operational efficiency. Companies might need to invest in new security measures and conduct thorough investigations to prevent future incidents.
Understanding these effects highlights the importance of having strong security measures and a solid incident response plan in place. By proactively addressing potential risks, businesses can minimize the impact of exfiltration and protect their assets.
Common Signs of Exfiltration in Incident Response
Recognizing common signs of exfiltration in incident response can help you detect data theft early. Look for unusual data transfers or spikes in network activity that may indicate unauthorized access. Monitoring these patterns can alert you to potential breaches.
Another sign is abnormal user behavior, such as accessing large amounts of data or unusual login times. Employees or attackers engaging in these activities could be attempting to exfiltrate information. Keeping an eye on user activities and access logs can help you identify suspicious behavior.
System alerts and notifications can also signal potential exfiltration. Ensure that your security tools are configured to send alerts for any anomalies or suspicious activities. Promptly investigating these alerts can help you respond quickly to prevent data loss.
Understanding Exfiltration in Incident Response: What You Need to Know
Understanding exfiltration in incident response is essential for safeguarding your organization’s data. It involves knowing how data can be stolen during a security incident and implementing measures to prevent it. Exfiltration in incident response article This knowledge helps you stay prepared and protect your sensitive information.
Familiarize yourself with the different methods of exfiltration and how attackers use them. This includes phishing, malware, and exploiting system vulnerabilities. By learning about these techniques, you can better defend against them and minimize the risk of data theft.
Additionally, understanding the impact of exfiltration on your organization helps in developing effective response strategies. Knowing the potential consequences allows you to prioritize security measures and focus on protecting your most valuable assets.
Exfiltration in Incident Response: Tips for Small Businesses
Exfiltration in incident response can be particularly challenging for small businesses with limited resources. However, there are several tips that can help you protect your data and respond effectively to potential breaches.
Start by implementing basic security measures like strong passwords, regular software updates, and firewalls. Even small steps can significantly enhance your security posture and reduce the risk of data exfiltration.
Training employees on cybersecurity best practices is also crucial. Make sure your team is aware of common threats and knows how to handle sensitive information securely. Regular training can help prevent accidental data breaches and improve your overall security.
How to Train Your Team About Exfiltration in Incident Response
Training your team about exfiltration in incident response is vital for preventing data theft. Start by educating employees about the risks and methods of data exfiltration. Exfiltration in incident response article This includes explaining how attackers might try to steal information and what signs to watch for.
Provide practical training sessions on how to recognize phishing emails and other common attack methods. Role-playing exercises and real-life examples can help employees understand how to respond to potential threats.
Regularly updating training materials and conducting refresher courses ensures that your team stays informed about the latest threats and security practices. Effective training helps build a strong defense against data exfiltration and enhances your organization’s overall security.
Exfiltration in Incident Response: Protecting Your Data
Protecting your data from exfiltration in incident response involves several key practices. First, implement strong access controls to limit who can view and handle sensitive information. Ensure that only authorized personnel have access to critical data.
Regularly monitor your network for signs of unusual activity. Using security tools like intrusion detection systems can help detect potential exfiltration attempts early and allow for prompt response.
Additionally, encrypting sensitive data adds an extra layer of protection. Encryption makes it much harder for attackers to read or use stolen information. By combining these practices, you can strengthen your defenses against data exfiltration.
Mitigating Risks from Exfiltration in Incident Response
Mitigating risks from exfiltration in incident response involves implementing proactive measures to protect your data. Start by regularly assessing your security posture and identifying potential vulnerabilities. Addressing these weaknesses can reduce the risk of data theft.
Develop a comprehensive incident response plan that includes specific steps for dealing with exfiltration. This plan should outline how to detect, contain, and recover from data breaches, ensuring that your team is prepared for any situation.
Regularly testing and updating your security measures is also important. Conducting simulations and reviewing past incidents can help you refine your strategies and improve your ability to respond to future threats effectively.
Case Studies of Exfiltration in Incident Response
Case studies of exfiltration in incident response provide valuable lessons on how data theft can impact organizations. By examining real-world examples, you can learn from the experiences of others and apply these insights to your own security practices.
One case study might involve a company that suffered a data breach due to a vulnerability in their network. Analyzing how the breach occurred and how the company responded can reveal important lessons about improving security and preventing similar incidents.
Another case study could focus on the steps taken by an organization to recover from a data exfiltration incident. Understanding their recovery process and the challenges they faced can provide useful guidance for developing your own incident response plan.
Improving Your Incident Response with Exfiltration Knowledge
Improving your incident response with exfiltration knowledge involves applying what you learn about data theft to strengthen your security measures. Start by incorporating insights from exfiltration in incident response articles into your incident response plan.
Regularly reviewing and updating your security practices based on new information can help you stay ahead of emerging threats. Use lessons learned from past incidents to refine your response strategies and improve your overall security posture.
Additionally, sharing knowledge and training your team on exfiltration can enhance your organization’s readiness. By keeping everyone informed and prepared, you can better handle data theft incidents and protect your sensitive information.
How to Handle Exfiltration in Incident Response Incidents
Handling exfiltration in incident response incidents requires a clear and organized approach. Start by immediately detecting and containing the breach to prevent further data loss. Use your incident response plan to guide your actions and ensure that all necessary steps are taken.
Once the breach is contained, focus on analyzing the incident to understand how it happened and what data was affected. This analysis will help you identify any gaps in your security and improve your defenses.
Finally, communicate with stakeholders and regulatory bodies about the incident. Transparency is important for maintaining trust and complying with legal requirements. By following these steps, you can effectively manage and recover from exfiltration incidents.
Future Trends in Exfiltration in Incident Response
Future trends in exfiltration in incident response involve evolving techniques and new challenges in data security. As technology advances, so do the methods used by attackers to steal data. Staying informed about these trends can help you anticipate and prepare for future threats.
Emerging technologies like artificial intelligence and machine learning are being used by both attackers and defenders. Understanding how these technologies impact data exfiltration can help you adapt your security strategies and stay ahead of potential risks.
Additionally, increasing regulatory requirements and public awareness about data security are shaping the future of incident response. Keeping up with these developments will help you ensure that your organization remains compliant and effective in handling data breaches.
Conclusion
Exfiltration in incident response article is a big deal because it shows how important it is to protect our data. When attackers steal information, it can cause a lot of problems for businesses and people. By learning about how exfiltration happens and following the tips from articles, we can better defend our data and keep it safe.
Remember, staying informed and having a good plan in place is key to preventing and handling data theft. Keeping your systems secure, training your team, and using the right tools will help you respond to exfiltration quickly. By taking these steps, you can help ensure that your data remains protected and secure.
